Ingest Scan Results from Snyk
This workflow describes how to ingest Snyk scan results into a Harness pipeline. STO supports the following scan approaches for the following Snyk products:
- Snyk Open Source (orchestratedScan, ingestionOnly)
- Snyk Code (ingestionOnly)
- Snyk Container (ingestionOnly)
Important notes
You must have a Snyk API key to run Snyk scans. You should also create a Harness secret for your API key.
This workflow assumes you're familiar with the following:
Setup requirements for AWS CodePipeline
Check this page in the Snyk docs to see if you need to build the project before scanning. These requirements are applicable to Harness pipelines as well as AWS CodePipeline.
Workflow Example
The following example describes how to scan a local .NET image built using Mavan. A Run step installs the build; then it scans the image and saves the output to a shared folder. A Security step then ingests the output file.
In your Harness pipeline, go to the Overview tab of the Security stage. Under Shared Paths, enter a shared path such as
/shared/customer_artifacts.Add a Run step that runs the build (if required) and saves the results to the shared folder:
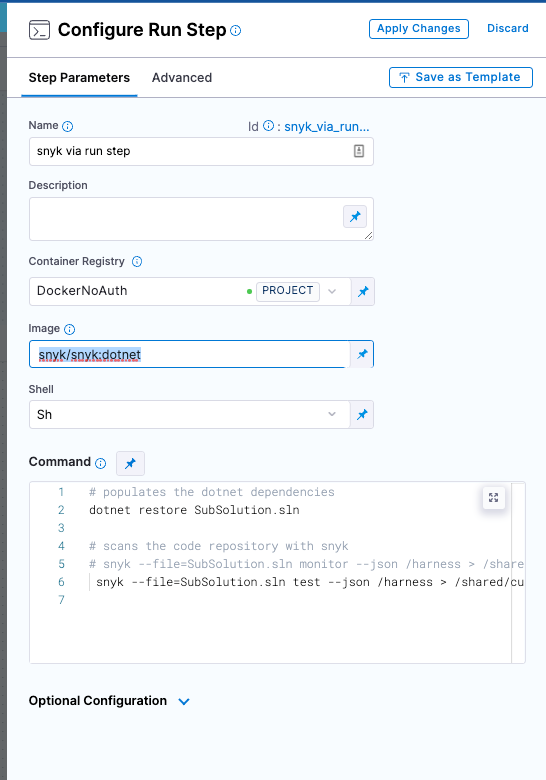
For the Run step Image, use a supported Snyk image based on the type of code in your codebase.
In the Run step Command field, add code to build a local image (if required) and save the scan results to the shared folder.
You can run a scan in this step or copy results from an external scan. In either case, the results file needs to be in the
/shared/customer_artifacts/folder where the Security step can access it.In this example, the Run step populates the DotNet dependencies, scans the code repository with Snyk, and saves the output to
/shared/customer_artifacts/SubSolution.json.dotnet restore SubSolution.sln
snyk --file=SubSolution.sln test --json /harness > /shared/customer_artifacts/SubSolution.jsonIn the Run step Environment Variables field, under Optional Configuration, add a variable to access your Snyk API key:
SNYK_TOKEN=<+secrets.getValue("snyk_api_token")>Your Run step should now look like this:
In the Run step > Advanced tab > Failure Strategies, set the Failure Strategy to Mark as Success.
This step is required to ensure that the pipeline proceeds if Snyk finds a vulnerability. Otherwise the build will exit with a error code before STO can ingest the data.
Add a Security step and configure the scanner to ingest the results of the scan. In this example, the step is configured as follows:
- step:
type: Security
name: snyk
identifier: snyk
spec:
privileged: true
settings:
policy_type: ingestionOnly
scan_type: repository
product_name: snyk
product_config_name: default
repository_project: SubSolution
repository_branch: <+codebase.branch>-<+codebase.tag>
customer_artifacts_path: /shared/customer_artifacts
manual_upload_filename: SubSolution.json
imagePullPolicy: Always