Ingest SARIF results
Static Analysis Results Interchange Format (SARIF) is an open data format supported by many scan tools, especially tools available as GitHub Actions. You can easily ingest SARIF 2.1.0 data from any tool that supports this format.
The following workflow describes how to set up an ingestion pipeline for any scanner that supports SARIF.
Ingestion workflow description
In your Harness pipeline, go to the Overview tab of the security stage and enter a shared path such as
/shared/customer_artifacts.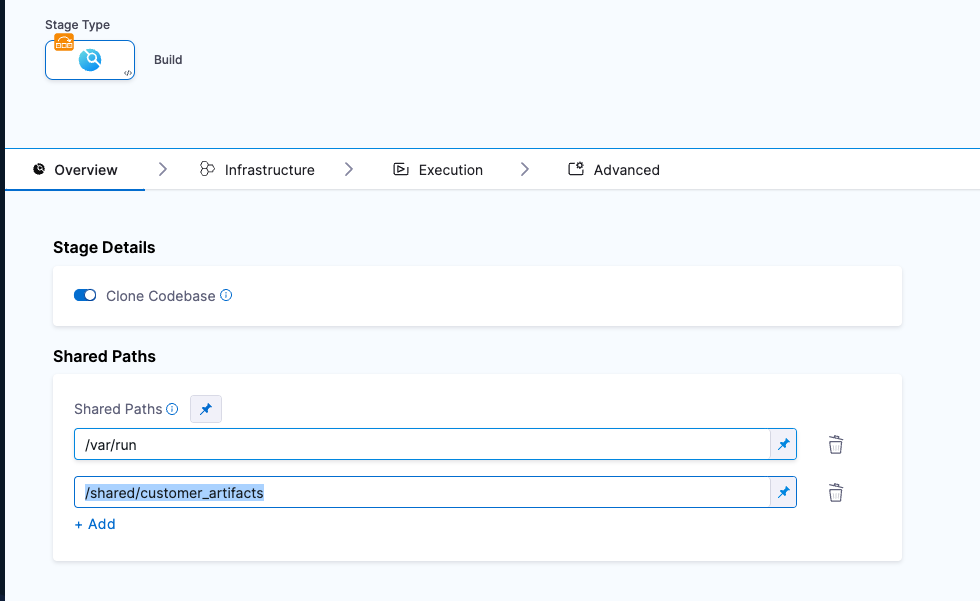
Publish your scan results to a data file in SARIF 2.1.0 format.
You might want to set up a Run step to generate your scans automatically whenever the pipeline runs.
Copy the SARIF file to the
/shared/customer_artifactsfolder.Add an ingestion step after the Run step and configure it as follows.
If you're using a scanner that has a scanner template, use the scanner template to ingest your results. Otherwise use a Custom Ingest step.
Ingestion settings
Target Name
The Identifier that you want to assign to the target you’re scanning in the pipeline. Use a unique, descriptive name such as codebaseAlpha or jsmith/myalphaservice. Using descriptive target names will make it much easier to navigate your scan data in the STO UI.
Target Variant
An identifier for a specific variant to scan, such as the branch name or image tag. This identifier is used to differentiate or group results for a target. Harness maintains a historical trend for each variant.
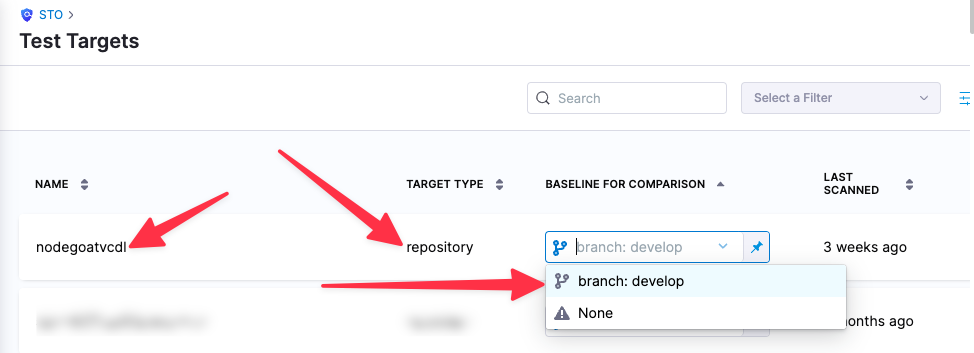
You can see the target name, type, and variant in the Test Targets UI:
Ingestion File
The results data file to use when running an Ingestion scan. STO steps can ingest scan data in SARIF and Harness Custom JSON format. Generally an Ingestion scan consists of a scan step (to generate the data file) and an ingestion step (to ingest the data file).
Fail on Severity
Every Security step has a Fail on Severity setting. If the scan finds any vulnerability with the specified severity level or higher, the pipeline fails automatically. You can specify one of the following:
CRITICALHIGHMEDIUMLOWINFONONE— Do not fail on severity
The YAML definition looks like this: fail_on_severity : critical # | high | medium | low | info | none
Example workflows
For example workflows that show how you can ingest SARIF data, go to Run scans using GitHub Action and Drone Plugin steps