AWS Lambda
This tutorial demonstrates how to deploy on AWS Lambda using Harness Continuous Delivery (CD). We will guide you through deploying a sample function using a Harness pipeline.
- Serverless.com Infrastructure
- Native AWS Lambda
Before you begin
Verify the following:
Obtain GitHub personal access token with the repo scope. For the GitHub documentation, go to creating a personal access token.
Docker. For this tutorial ensure that you have the Docker runtime installed on your Harness delegate host. If not, use one of the following options to install Docker:
Fork the harnessed-example-apps repository through the GitHub website.
- For more information on forking a GitHub repository, go to GitHub docs.
AWS user account with required policy: Serverless deployments require an AWS user account with specific AWS permissions, as described in AWS Credentials from Serverless.com. To create the AWS user, do the following in AWS IAM:
Select Users, and then Add user. Enter a name. Enable Programmatic access by selecting the checkbox. Select Next to go to the Permissions page. Do one of the following:
- Full Admin Access: select Attach existing policies directly. Search for and select AdministratorAccess then select Next: Review. Check to make sure everything looks good and select Create user.
- Limited Access: select Create policy. Select the JSON tab, and add the JSON from the Serverless gist: IAMCredentials.json.
Supported platforms and versions
- Harness supports Serverless framework 1.82 and later.
- Harness supports Serverless framework CLI versions 2.x.x and 3.x.x.
- Harness supports all language runtimes that Serverless supports.
- Harness supports ZIP files and Docker image artifacts only.
- ZIP files are supported with JFrog Artifactory.
- Docker images are supported with AWS ECR.
Getting Started with Harness CD
- Log into Harness.
- Select Projects and choose Default Project.
Going forward, follow all the steps as they are, including the naming conventions, for the pipeline to run successfully.
Delegate
What is the Harness delegate?
The Harness delegate is a service that runs in your local network or VPC to establish connections between the Harness Manager and various providers such as artifacts registries, cloud platforms, etc. The delegate is installed in the target infrastructure, for example, a Kubernetes cluster, and performs operations including deployment and integration. Learn more about the delegate in the Delegate Overview.
- Under Project Setup, select Delegates.
- In Delegates Setup, select Install new Delegate. The delegate wizard appears.
- In New Delegate, in Select where you want to install your Delegate, select Docker.
- Enter the delegate name,
harness-aws-lambda-delegate.
Now you can install the delegate by using the command that appears on your installation wizard. The command is prefilled with the information for the environment variables in the example below.
docker run --cpus=1 --memory=2g \
-e DELEGATE_NAME=harness-serverless-delegate \
-e NEXT_GEN="true" \
-e DELEGATE_TYPE="DOCKER" \
-e ACCOUNT_ID= YOUR_HARNESS_ACCOUNTID \
-e DELEGATE_TOKEN=YOUR_DELEGATE_TOKEN \
-e LOG_STREAMING_SERVICE_URL=YOUR_MANAGER_HOST_AND_PORT/log-service/ \
-e MANAGER_HOST_AND_PORT=YOUR_MANAGER_HOST_AND_PORT \
DELEGATE_IMAGE:TAG
Replace DELEGATE_IMAGE:TAG with the custom delegate image harnesscommunity/serverless-delegate:latest. This image has the Serverless.com framework installed.
Verify delegate connectivity
- Select Continue. After the health checks passes, your delegate is available to use.
- Select Done and verify your new delegate is listed.
Secrets
What are Harness secrets?
Harness offers built-in secret management for encrypted storage of sensitive information. Secrets are decrypted when needed, and only the private network-connected Harness delegate has access to the key management system. You can also integrate your own secret manager. To learn more about secrets in Harness, go to Harness Secret Manager Overview.
Github secret
- Under Project Setup, select Secrets.
- Select New Secret, and then select Text.
- Enter the secret name
harness_gitpat. - For the secret value, paste the GitHub personal access token you saved earlier.
- Select Save.
AWS secret
- Select New Secret, and then select Text.
- Enter the secret name
aws_access_key. - For the secret value, paste the access token for your AWS user account. The Harness delegate uses this credential to authenticate Harness with AWS at deployment runtime.
- Select Save.
Connectors
What are connectors?
Connectors in Harness enable integration with 3rd party tools, providing authentication for operations during pipeline runtime. For instance, a GitHub connector facilitates authentication and fetching files from a GitHub repository within pipeline stages. For more details, go to Connectors.
Create the GitHub connector.
- Copy the contents of github-connector.yml.
- In your Harness project in the Harness Manager, under Project Setup, select Connectors.
- Select Create via YAML Builder and paste the copied YAML.
- Assuming you have already forked the harnessed-example-apps repository mentioned earlier, replace
GITHUB_USERNAMEin the YAML with your GitHub account username. - In
projectIdentifier, replace with the project identifier with yours, for example,default. - Select Save Changes and verify that the new connector named harness_gitconnector is successfully created.
- Finally, select Connection Test under Connectivity Status to ensure the connection is successful.
Create the AWS Connector.
- Copy the contents of aws-connector.yml.
- In your Harness project in the Harness Manager, under Project Setup, select Connectors.
- Select Create via YAML Builder and paste the copied YAML.
- Assuming you have already forked the harnessed-example-apps repository mentioned earlier, replace
crossAccountRoleArnin the YAML with your AWS role's ARN. - Replace the
accessKeyplaceholder with the AWS access key for the AWS user you created (with the required policies). - Here we assume the
regionfor secret key to beus-east-1. Please replace it with the appropriate region. - In
projectIdentifier, replace with the project identifier with yours, for example,default. - Select Save Changes and verify that the new connector named harness_awsconnector is successfully created.
- Finally, select Connection Test under Connectivity Status to ensure the connection is successful.
Environment
What are Harness environments?
Environments define the deployment location, categorized as Production or Pre-Production. Each environment includes infrastructure definitions for serverless functions, VMs, Kubernetes clusters, or other target infrastructures. To learn more about environments, go to Environments overview.
- In your Harness project, select Environments.
- Select New Environment, and then select YAML.
- Copy the contents of environment.yml, paste it into the YAML editor, and select Save.
- In your new environment, select the Infrastructure Definitions tab.
- Select Infrastructure Definition, and then select YAML.
- Copy the contents of infrastructure-definition.yml and paste it into the YAML editor.
- Select Save and verify that the environment and infrastructure definition are created successfully.
Services
What are Harness services?
In Harness, services represent what you deploy to environments. You use services to configure variables, manifests, functions, and artifacts. The Services dashboard provides service statistics like deployment frequency and failure rate. To learn more about services, go to Services overview.
- In your Harness project, select Services.
- Select New Service.
- Enter the name
harnessserverless. - Select Save, and then YAML (on the Configuration tab).
- Select Edit YAML, copy the contents of service.yml, and paste the into the YAML editor.
- Select Save and verify that the service harness_serverless is successfully created.
Pipeline
What are Harness pipelines?
A pipeline is a comprehensive process encompassing integration, delivery, operations, testing, deployment, and monitoring. It can utilize CI for code building and testing, followed by CD for artifact/function deployment in production. A CD pipeline is a series of stages where each stage deploys a service to an environment. To learn more about CD pipeline basics, go to CD pipeline basics.
- In your Harness project, select Pipelines.
- Select Create a Pipeline.
- Enter the name
serverless_pipeline. - Choose Inline to store the pipeline in Harness.
- Select Start.
- In Pipeline Studio, select YAML.
- Select Edit YAML and paste in the YAML in the next section.
Deploy AWS Lambda using Serverless.com Framework
Copy the contents of serverless-pipeline.yml.
In your Harness pipeline YAML editor, paste the YAML.
Select Save.
You can switch to the Visual pipeline editor and confirm the pipeline stage and execution steps as shown below.
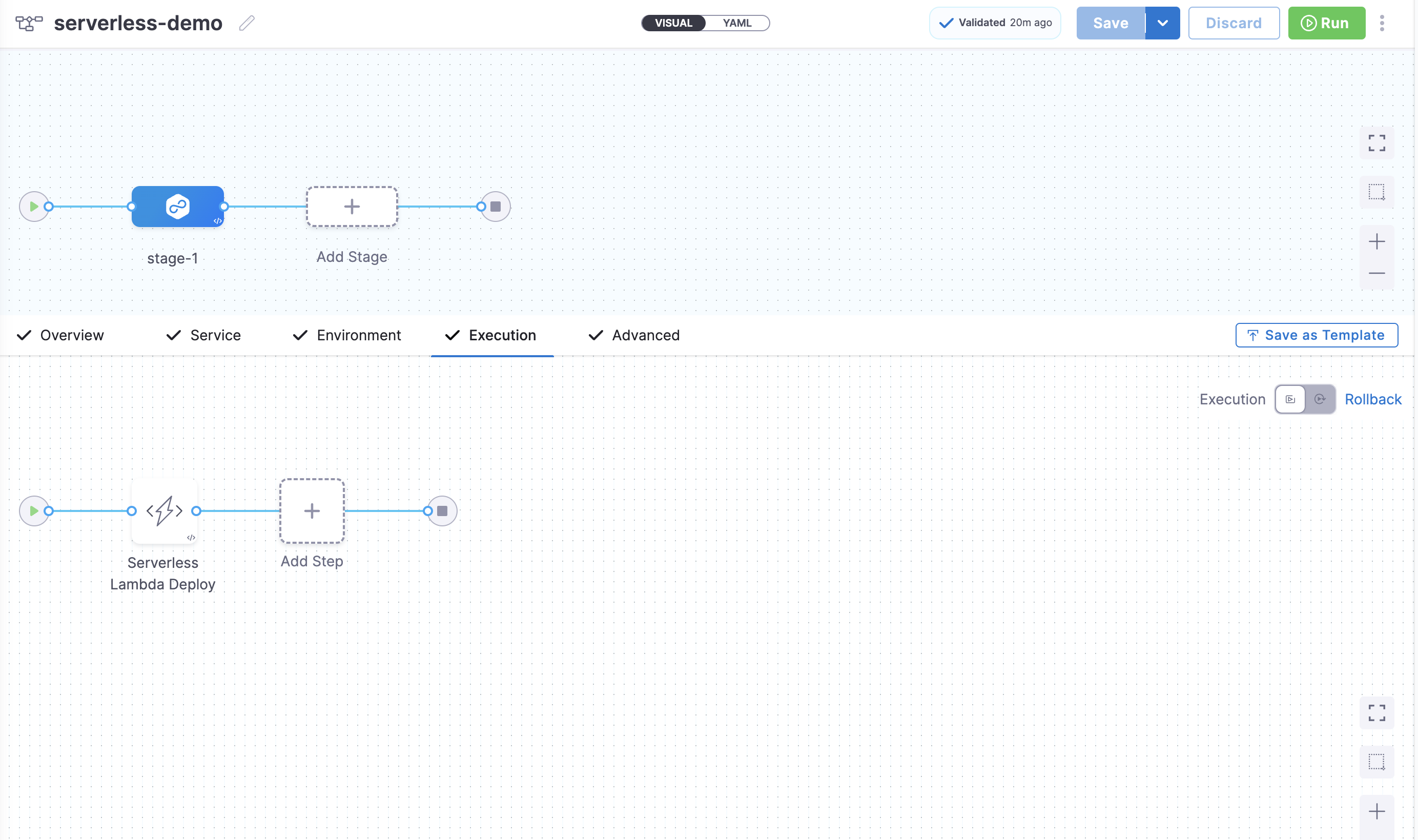
Finally, it's time to execute the pipeline. Select Run, and then select Run Pipeline to initiate the deployment.
Observe the execution logs as Harness deploys the function.
Congratulations!🎉
You've just learned how to use Harness CD to deploy an AWS Lambda function on AWS Lambda using the Serverless.com Framework.
Before you begin
Verify the following:
Obtain GitHub personal access token with the repo scope. For GitHub documentation, go to creating a personal access token.
Docker. For this tutorial ensure that you have the Docker runtime installed on your Harness delegate host. If not, use one of the following options to install Docker:
Fork the harnessed-example-apps repository through the GitHub website.
- For more information on forking a GitHub repository, go to GitHub docs.
AWS S3 bucket with the artifact, upload the hello-world.zip in a new s3 bucket, to be used as an artifact.
AWS user account with required policy: To deploy a Lambda function, you need an AWS Identity and Access Management (IAM) role with the necessary permissions. You will use that role in the credentials you supply to the Harness AWS connector.
In AWS IAM, select Users, and then Add user. Enter a name. Enable Programmatic access by selecting the checkbox. Select Next to go to the Permissions page. Do one of the following:
- Full Admin Access: select Attach existing policies directly. Search for and select AdministratorAccess then select Next: Review. Check to make sure everything looks good and select Create user.
- Limited Access: select Create policy and add the following minimum AWS IAM role policies that you would need to deploy a Lambda function:
- IAMReadOnlyAccess: Needed to verify required policies.
- AWSLambdaRole: Needed to invoke function.
- AWSLambda_FullAccess (previously AWSLambdaFullAccess): Needed to write to Lambda.
- AmazonS3ReadOnlyAccess: Needed to pull the function file from S3.
- AmazonEC2ContainerRegistryReadOnly: Needed to pull function container image from ECR. This policy provides read-only access to the ECR repository.
- AWS Lambda Execution Role: As a Lambda user, you probably already have the AWS Lambda Execution Role set up. If you do not, follow the steps in AWS Lambda Execution Role from AWS.
Example IAM policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "IAMReadOnlyAccess",
"Effect": "Allow",
"Action": [
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy"
],
"Resource": "*"
},
{
"Sid": "LambdaAccess",
"Effect": "Allow",
"Action": [
"lambda:CreateFunction",
"lambda:UpdateFunctionCode",
"lambda:UpdateFunctionConfiguration",
"lambda:PublishVersion",
"lambda:CreateAlias",
"lambda:Get*",
"lambda:List*",
"lambda:InvokeFunction",
"lambda:DeleteFunction",
"lambda:DeleteAlias",
"lambda:DeleteFunctionConcurrency",
"lambda:AddPermission",
"lambda:RemovePermission",
"lambda:EnableReplication",
"lambda:DisableReplication",
"lambda:GetFunctionCodeSigningConfig",
"lambda:UpdateFunctionCodeSigningConfig",
"lambda:GetCodeSigningConfig",
"lambda:ListCodeSigningConfigs",
"lambda:CreateCodeSigningConfig",
"lambda:DeleteCodeSigningConfig",
"lambda:UpdateFunctionEventInvokeConfig",
"lambda:GetFunctionEventInvokeConfig",
"lambda:ListFunctionsByCodeSigningConfig",
"lambda:ListTags",
"lambda:TagResource",
"lambda:UntagResource"
],
"Resource": "*"
},
{
"Sid": "S3ReadOnlyAccess",
"Effect": "Allow",
"Action": [
"s3:Get*",
"s3:List*"
],
"Resource": "*"
},
{
"Sid": "ECRReadOnlyAccess",
"Effect": "Allow",
"Action": [
"ecr:GetAuthorizationToken",
"ecr:BatchCheckLayerAvailability",
"ecr:GetDownloadUrlForLayer",
"ecr:GetRepositoryPolicy",
"ecr:DescribeRepositories",
"ecr:ListImages",
"ecr:DescribeImages",
"ecr:BatchGetImage"
],
"Resource": "*"
},
{
"Sid": "LambdaRoleAccess",
"Effect": "Allow",
"Action": [
"iam:PassRole"
],
"Resource": "arn:aws:iam::*:role/service-role/AWSLambdaExecutionRole"
}
]
}
Supported platforms and versions
- Harness can deploy a new Lambda function or update an existing Lambda function.
- Harness' support only deploys and updates Lambda functions. Harness does not update auxiliary event source triggers like the API Gateway, etc.
- Currently, Lambda functions can be packaged as ZIP files in S3 Buckets or as containers in AWS ECR.
- If Harness were to support another repository, like Nexus, when the container is fetched by the API, AWS spins up AWS resources (S3, ECR) anyways, and so Harness has limited support to S3 and ECR.
- The containers must exist in ECR. Containers are not supported in other repositories.
Getting Started with Harness CD
- Log into Harness.
- Select Projects, and then select Default Project.
For the pipeline to run successfully, please follow the remaining steps as they are, including the naming conventions.
Delegate
What is the Harness delegate?
The Harness delegate is a service that runs in your local network or VPC to establish connections between the Harness Manager and various providers such as artifacts registries, cloud platforms, etc. The delegate is installed in the target infrastructure, for example, a Kubernetes cluster, and performs operations including deployment and integration. Learn more about the delegate in the Delegate Overview.
- Under Project Setup, select Delegates.
- In Delegates Setup, select Install new Delegate. The delegate wizard appears.
- In New Delegate, in Select where you want to install your Delegate, select Docker.
Now you can install the delegate by using the command that appears on your installation wizard. The command is prefilled with the information for the environment variables as in the example below.
docker run --cpus=1 --memory=2g \
-e DELEGATE_NAME=docker-delegate \
-e NEXT_GEN="true" \
-e DELEGATE_TYPE="DOCKER" \
-e ACCOUNT_ID= YOUR_HARNESS_ACCOUNTID \
-e DELEGATE_TOKEN=YOUR_DELEGATE_TOKEN \
-e LOG_STREAMING_SERVICE_URL=YOUR_MANAGER_HOST_AND_PORT/log-service/ \
-e MANAGER_HOST_AND_PORT=YOUR_MANAGER_HOST_AND_PORT \
DELEGATE_IMAGE:TAG
You can also follow the Install Harness Delegate on Kubernetes tutorial to install the delegate using the Harness Terraform Provider or a Kubernetes manifest.
Verify delegate connectivity
- Select Continue. After the health checks passes, your delegate is available to use.
- Select Done and verify your new delegate is listed.
Secrets
What are Harness secrets?
Harness offers built-in secret management for encrypted storage of sensitive information. Secrets are decrypted when needed, and only the private network-connected Harness delegate has access to the key management system. You can also integrate your own secret manager. To learn more about secrets in Harness, go to Harness Secret Manager Overview.
- Under Project Setup, select Secrets.
- Select New Secret, and then select Text.
- Enter the secret name
harness_gitpat. - For the secret value, paste the GitHub personal access token you saved earlier.
- Select Save.
- Under Project Setup, select Secrets.
- Select New Secret, and then select Text.
- Enter the secret name
aws_permanent_access_key. - For the secret value, add the AWS Secret access key.
- Select Save.
Connectors
What are connectors?
Connectors in Harness enable integration with 3rd party tools, providing authentication and operations during pipeline runtime. For instance, a GitHub connector facilitates authentication and fetching files from a GitHub repository within pipeline stages. Explore connector how-tos here.
Create the GitHub connector.
- Copy the contents of github-connector.yml.
- In your Harness project in the Harness Manager, under Project Setup, select Connectors.
- Select Create via YAML Builder and paste the copied YAML.
- Assuming you have already forked the harnessed-example-apps repository mentioned earlier, replace
GITHUB_USERNAMEwith your GitHub account username in the YAML. - In
projectIdentifier, verify that the project identifier is correct. You can see the Id in the browser URL (afteraccount). If it is incorrect, the Harness YAML editor will suggest the correct Id. - Select Save Changes and verify that the new connector named harness_gitconnector is successfully created.
- Finally, select Connection Test under Connectivity Status to ensure the connection is successful.
Create the AWS Connector.
- Copy the contents of aws-connector.yml.
- In your Harness project in the Harness Manager, under Project Setup, select Connectors.
- Select Create via YAML Builder and paste the copied YAML.
- In
projectIdentifier, verify that the project identifier is correct. You can see the Id in the browser URL (afteraccount). If it is incorrect, the Harness YAML editor will suggest the correct Id. - Replace the
accessKeyplaceholder with the AWS access key for the AWS user you created (with the required policies). - Here we assume the
regionfor secret key to beus-east-1. Please replace it with the appropriate region. - Select Save Changes and verify that the new connector named harness_awsconnector is successfully created.
- Finally, select Connection Test under Connectivity Status to ensure the connection is successful.
Environment
What are Harness environments?
Environments define the deployment location, categorized as Production or Pre-Production. Each environment includes infrastructure definitions for serverless functions, VMs, Kubernetes clusters, or other target infrastructures. To learn more about environments, go to Environments overview.
- In your Harness project, select Environments.
- Select New Environment, and then select YAML.
- Copy the contents of environment.yml, paste it into the YAML editor, and select Save.
- In your new environment, select the Infrastructure Definitions tab.
- Select Infrastructure Definition, and then select YAML.
- Copy the contents of infrastructure-definition.yml and paste it into the YAML editor.
- Select Save and verify that the environment and infrastructure definition are created successfully.
Services
What are Harness services?
In Harness, services represent what you deploy to environments. You use services to configure variables, manifests, functions, and artifacts. The Services dashboard provides service statistics like deployment frequency and failure rate. To learn more about services, go to Services overview.
Function definition and function artifacts
What is AWS Lambda Function Definition?
Harness uses the AWS Lambda Create Function API to create a new Lambda function in the specified AWS account and region. In Harness, you use a JSON configuration file to define the AWS Lambda you wish to deploy. This configuration lets you define all the function settings supported by the Create Function API.
Setting up Lambda functions
- Assuming you have already forked the harnessed-example-apps repo, edit the function-definition.json file in your fork and add the ARN for your role having full AWS Lambda access in which you want to deploy the serverless application.
- In your Harness project, select Services.
- Select New Service.
- Enter the name
harnessserverless. - Select Save, and then YAML (on the Configuration tab).
- Select Edit YAML, copy the contents of service.yml, and paste the into the YAML editor.
- Mention the
bucket nameandregionwhere you uploaded the artifact in the beginning. - Select Save and verify that the service harness_serverless is successfully created.
Pipeline
What are Harness pipelines?
A pipeline is a comprehensive process encompassing integration, delivery, operations, testing, deployment, and monitoring. It can utilize CI for code building and testing, followed by CD for artifact/function deployment in production. A CD pipeline is a series of stages where each stage deploys a service to an environment. To learn more about CD pipeline basics, go to CD pipeline basics.
- In your Harness project, select Pipelines.
- Select Create a Pipeline.
- Enter the name
native-aws-lambda. - Choose Inline to store the pipeline in Harness.
- Select Start.
- In Pipeline Studio, select YAML.
- Select Edit YAML and paste in the YAML in the next section.
Deploy the serverless application on AWS Lambda
Copy the contents of pipeline.yml.
In your Harness pipeline YAML editor, paste the YAML.
Select Save.
You can switch to the Visual pipeline editor and confirm the pipeline stage and execution steps as shown below.
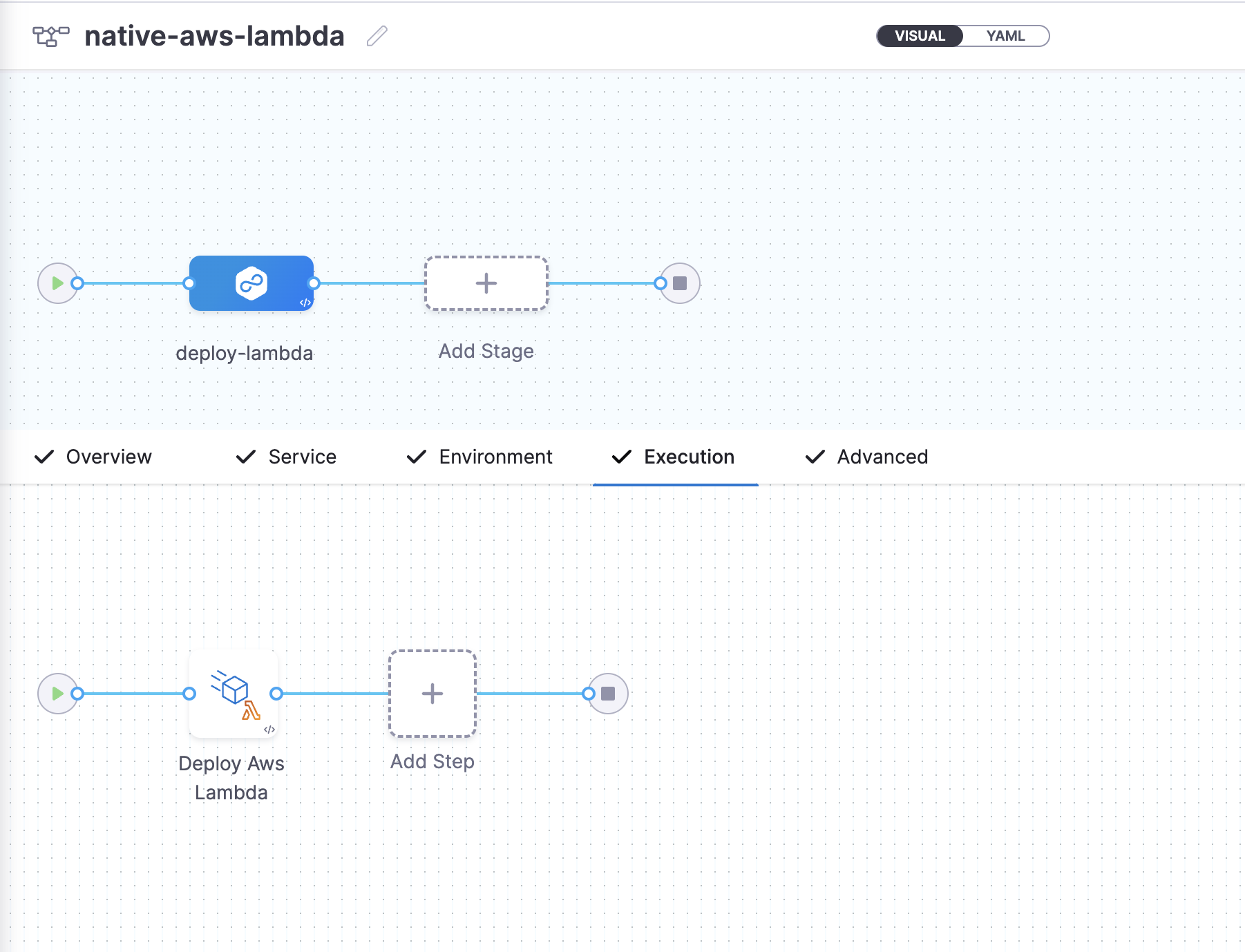
Finally, it's time to execute the Pipeline. Select Run.
Enter the Primary Artifact name and File Path for the artifact.
Select Run Pipeline to initiate the deployment.
Observe the execution logs as Harness deploys the function.
Congratulations!🎉
You've just learned how to use Harness CD to deploy an AWS Lambda function on AWS Lambda.