Add an Azure Key Vault Secrets Manager
This content is for Harness FirstGen. Switch to NextGen.This topic outlines how to use Azure Key Vault to maintain your Harness secrets. It includes these sections:
- Before You Begin
- Visual Overview
- Step 1: Create Azure Reader Role
- Step 2: Configure Secrets Manager in Harness
- Step 3: Set Display Name
- Step 4: Select Environment
- Step 5: Enter Client ID and Tenant ID
- Option: Enter Subscription
- Step 6: Create and Exchange Authentication Key
- Step 7: Fetch Vault
- Step 8: Usage Scope
- Step 9: Save the Secrets Manager
- Step 10: Make Key Vaults Writable
- Option: Use Existing Azure Key Vault Secrets
- Next Steps
Before You Begin
- Review Secrets Management for Harness' overall approach to managing secrets.
- Review Microsoft's documentation as necessary, starting with What Is Azure Key Vault? and Azure Key Vault Basic Concepts.
- We assume that you have an Azure account set up and ready to use.
- Make sure that the Harness Delegate is able to connect to this URL:
https://<vault_name>.vault.azure.net<vault_name>is the name of the vault selected from the dropdown while configuring the Azure Vault.
Visual Overview
Azure Key Vault safeguards cryptographic keys and secrets, encrypting authentication keys, storage account keys, data encryption keys, .pfx files, and passwords.
Step 1: Create Azure Reader Role
To enable Harness to later fetch your Azure vaults (in Step 7 below), you must first set up a Reader role in Azure. You can do this two ways:
Azure Portal
To create a Reader role in the Azure portal UI:
Navigate to Azure's Subscriptions page.
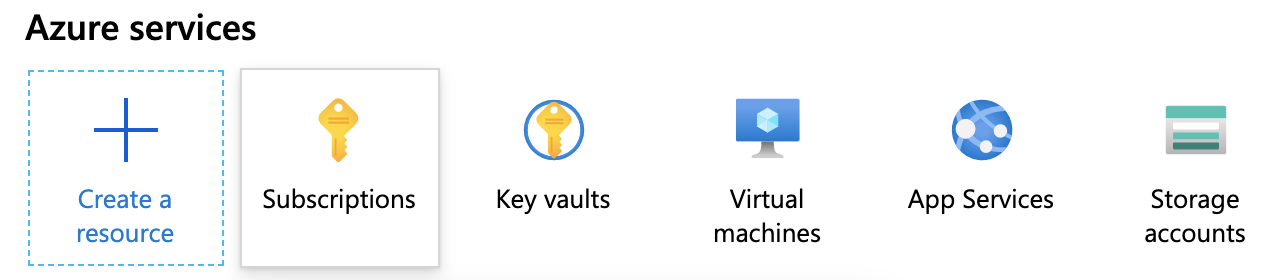
Under Subscription name, select the subscription where your vaults reside.
 Tip: Copy and save the Subscription ID. You can paste this value into Harness Manager below at Option: Enter Subscription.
Tip: Copy and save the Subscription ID. You can paste this value into Harness Manager below at Option: Enter Subscription.Select your Subscription’s Access control (IAM) property.
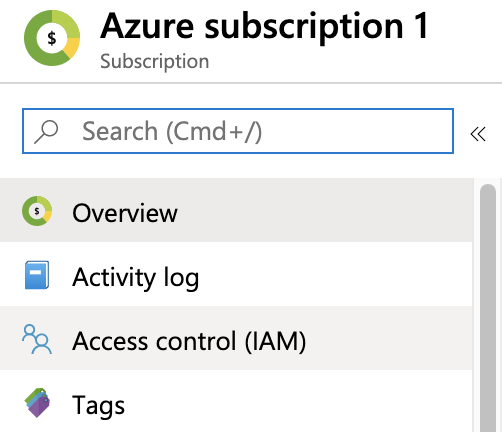
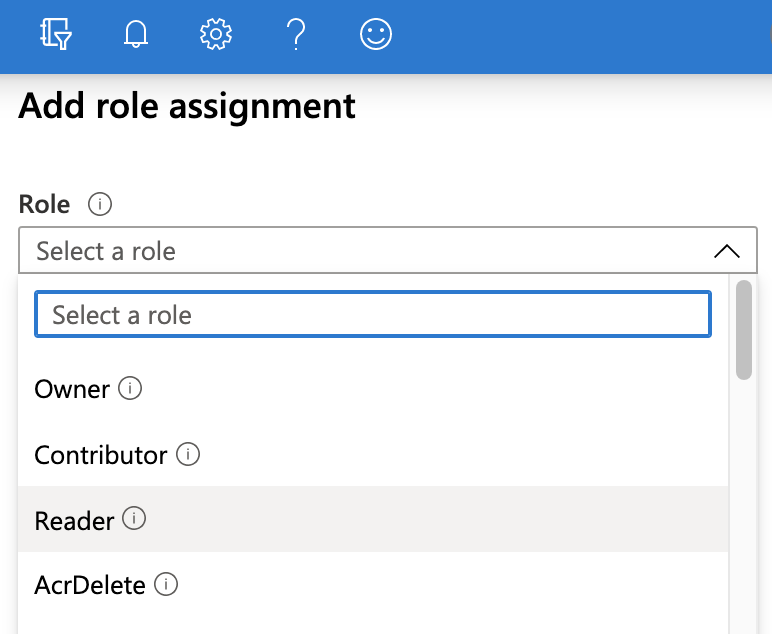
On the resulting Access control (IAM) page, select Add a role assignment.
In the resulting right pane, set the Role to Reader.
Accept the default value: Assign access to: Azure AD user, group, or service principal.
In the Select drop-down, select the name of your Azure App registration.
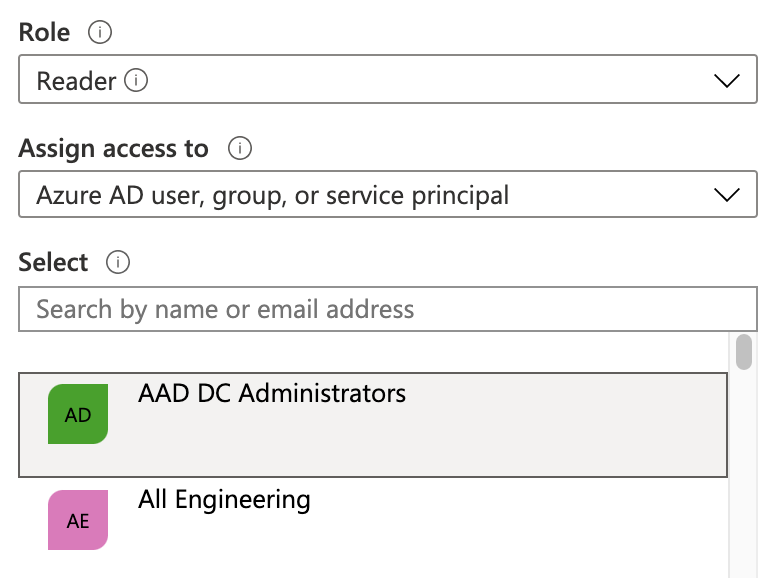
Click Save.
On the Access control (IAM) page, select the Role assignments tab. Make sure your new role now appears under the Reader group.

Microsoft Azure's Manage subscriptions documentation adds details about the above procedure, but focuses on the Administrator rather than the Reader role.
PowerShell Command
You can also create a Reader role programmatically via this PowerShell command, after gathering the required parameters:
New-AzRoleAssignment -ObjectId <object_id> -RoleDefinitionName "Reader" -Scope /subscriptions/<subscription_id>
For details and examples, see Microsoft Azure's Add or remove role assignments documentation.
Step 2: Configure Secrets Manager in Harness
To set up Azure Key Vault as a Harness Secrets Manager:
- In Security, select Secrets Management, and then click Configure Secrets Managers.
In the resulting Secrets Managers page, the Status column indicates the Default provider. - Click Add Secrets Manager. The Configure Secrets Manager settings appear.
- Select Azure Key Vault from the drop-down list.
Key Vault stores and manages secrets as sequences of octets (8-bit bytes), with a maximum size of 25k bytes each. For more information, see Azure Key Vault secrets.If you set up Azure Key Vault as your default secrets manager in Harness, any secret that you save afterwards must be named according to Azure Key Vault conventions.
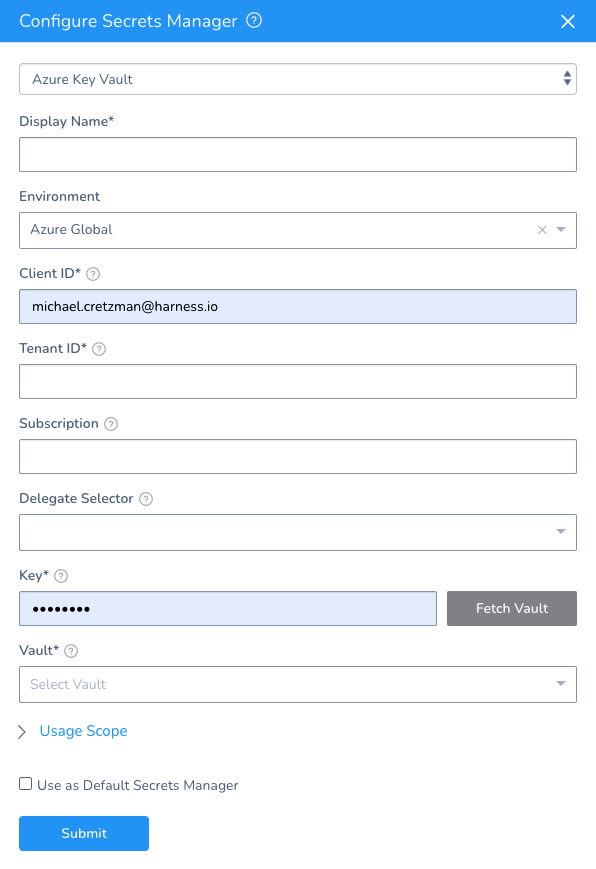
Step 3: Set Display Name
In the Configure Secrets Manager dialog's Display Name field, enter an arbitrary name to identify this key vault within Harness Manager.
Step 4: Select Environment
Harness supports Azure Government (Gov Cloud) and Azure Global (global Azure) environments. You can read about their differences in Compare Azure Government and global Azure from Azure.
In Environment, select Azure Global or US Government. Most accounts use Azure Global.
Step 5: Enter Client ID and Tenant ID
This dialog's Client ID and Tenant ID entries correspond to the fields highlighted below in the Azure UI:
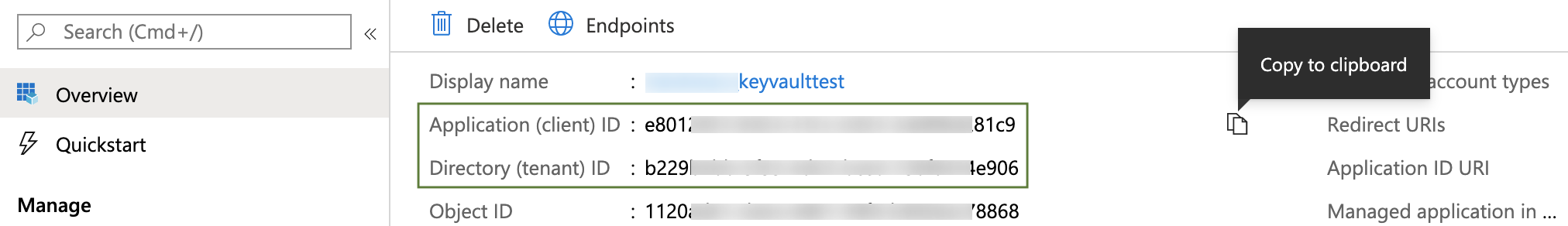 To provide these values:
To provide these values:
- In Azure, navigate to the Azure Active Directory > App registrations page, then select your App registration. (For details, see Azure's Quickstart: Register an application with the Microsoft identity platform.)
- Copy the Application (client) ID for the Azure App registration you are using, and paste it into the Harness dialog's Client ID field.
- Copy the Directory (tenant) ID of the Azure Active Directory (AAD) where you created your application, and paste it into the Harness dialog's Tenant ID field. (For details, see Microsoft Azure's Get values for signing in topic.)
Option: Enter Subscription
In the Subscription field, you can optionally enter your Azure Subscription ID (GUID).
To find this ID, navigate to Azure's Subscriptions page, as outlined above in Step 1: Create Azure Reader Role. From the resulting list of subscriptions, copy the Subscription ID beside the subscription that contains your vaults.
 If you do not enter a GUID, Harness uses the default subscription for the Client ID you've provided above.
If you do not enter a GUID, Harness uses the default subscription for the Client ID you've provided above.
Step 6: Create and Exchange Authentication Key
Generate an authentication key in Azure, and add it to Harness Manager as an application password:
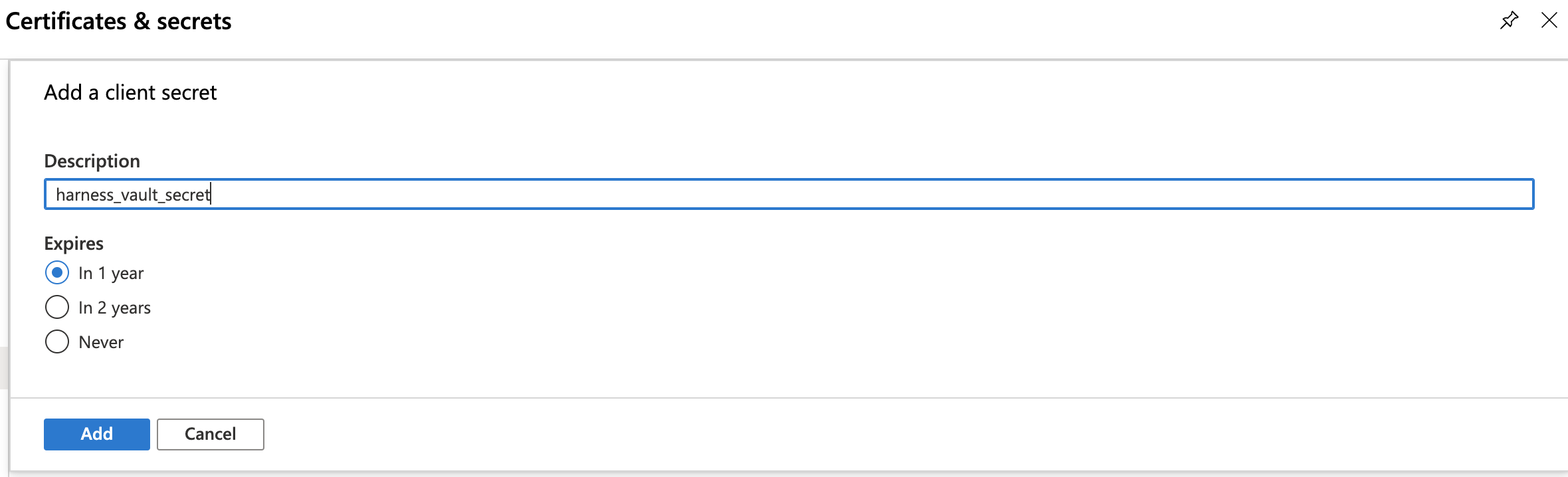
Navigate to Azure's Certificates & secrets page. (For details, see Microsoft Azure's Create a new application secret documentation.)
In the resulting page’s Client secrets section, select New client secret.
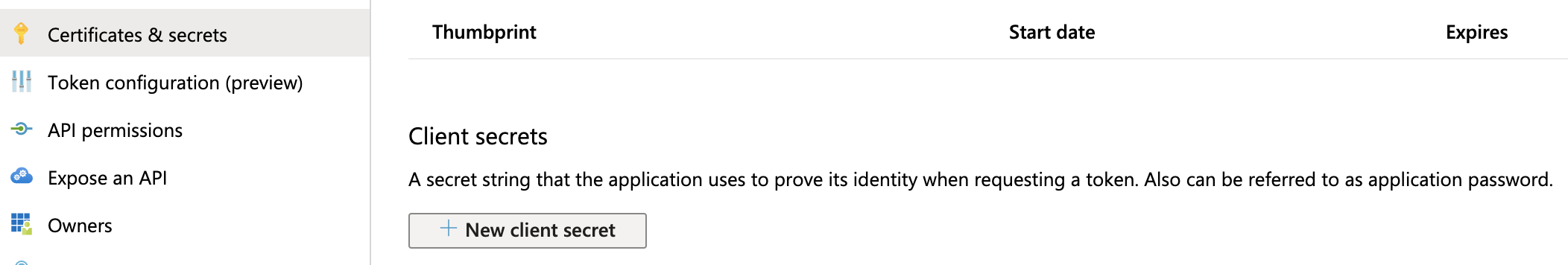
Enter a Description and expiration option, then click Add.
Find your new key in the Client secrets section, and copy its value to your clipboard.
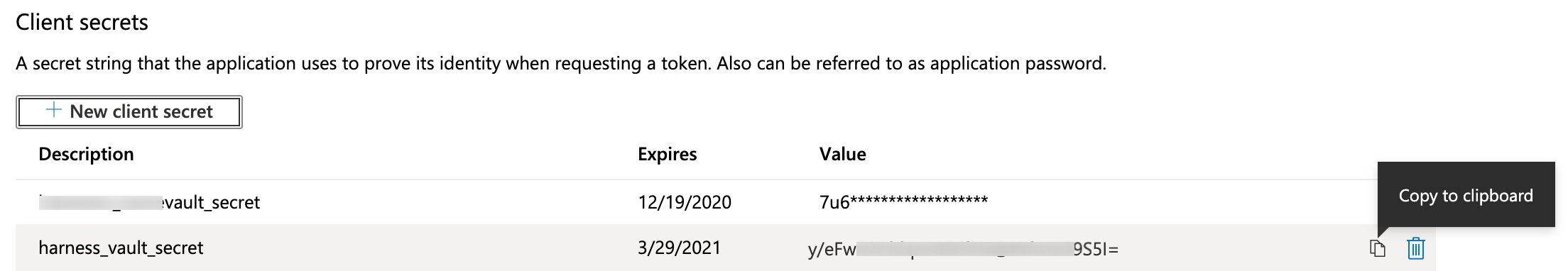 This is your only chance to view this key's value in Azure. Store the value somewhere secure, and keep it on your clipboard.
This is your only chance to view this key's value in Azure. Store the value somewhere secure, and keep it on your clipboard.Paste the key into Harness’ Key field.
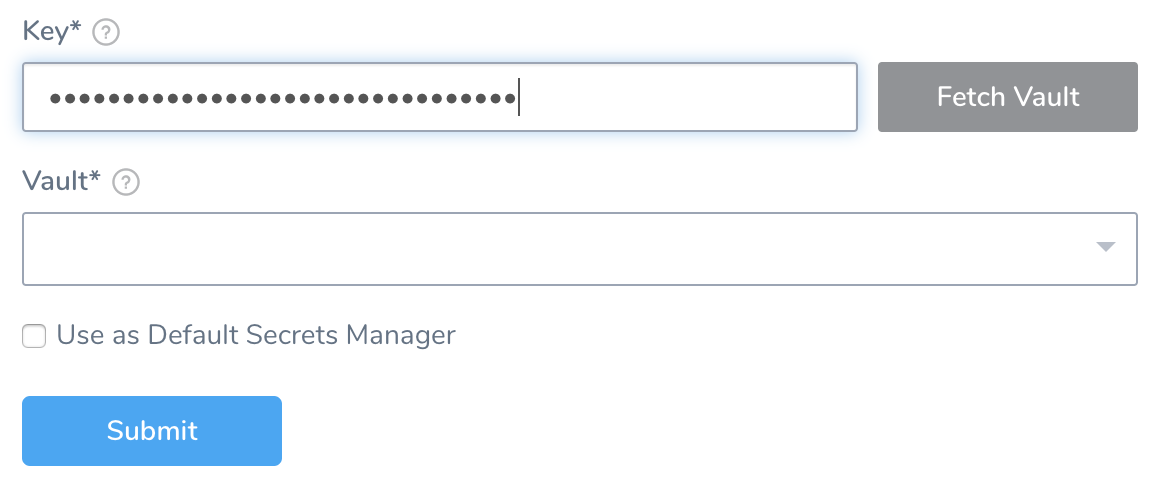
Step 7: Fetch Vault
Click Fetch Vault.
After a slight delay, the Vault drop-down list populates with vaults corresponding to your client secret.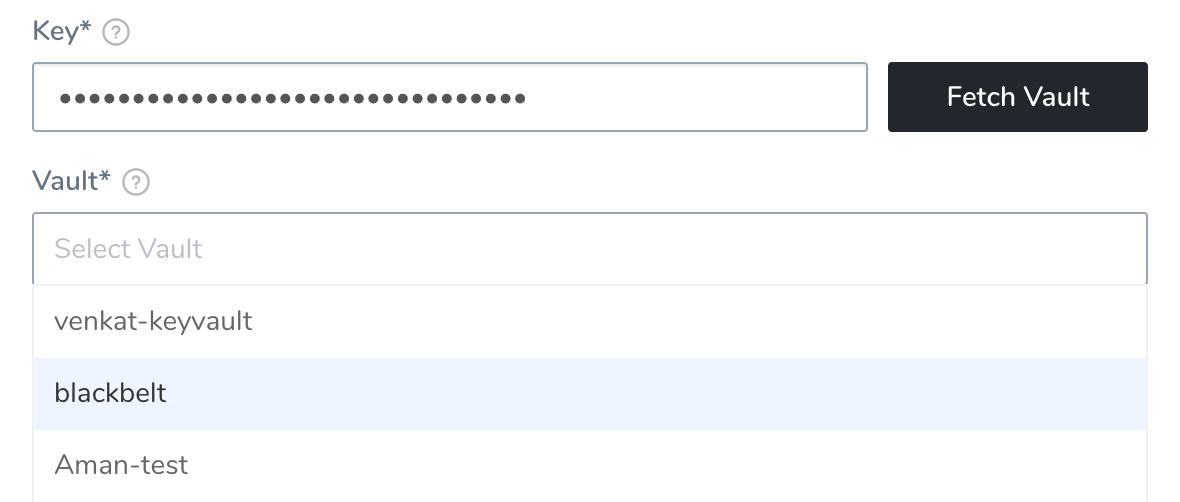
From the Vault drop-down, select the vault to use.
If these controls do not respond as expected, double-check whether you have successfully configured Step 1: Create Azure Reader Role above.
Step 8: Usage Scope
See Scope Secret Managers to Applications and Environments.
Step 9: Save the Secrets Manager
- If you choose to make Azure Key Vault your Harness default, select Use as Default Secrets Manager.
- To save your configured Secrets Manager, click Submit.Harness does not validate your configuration upon save.
Step 10: Make Key Vaults Writable
For every key vault that you'll want to write to, you must follow this procedure:
Navigate to Azure 's Key vaults page.
Select the Vault instance that matches Harness Manager's Vault field.
Select Settings > Access policies.
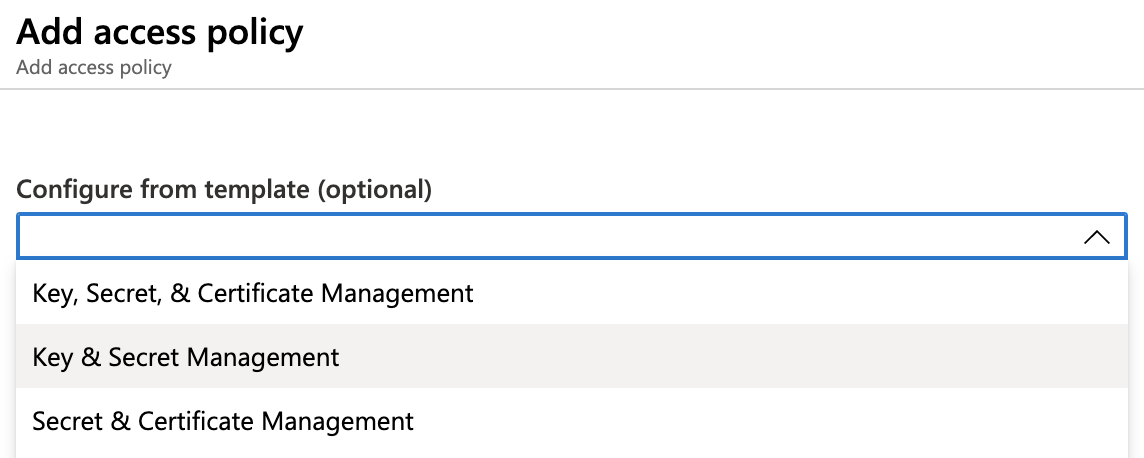
In the Access policies page’s main area, click Add access policy.
On the resulting Add access policy page, use the Configure from template drop-down to select Key & Secret Management.
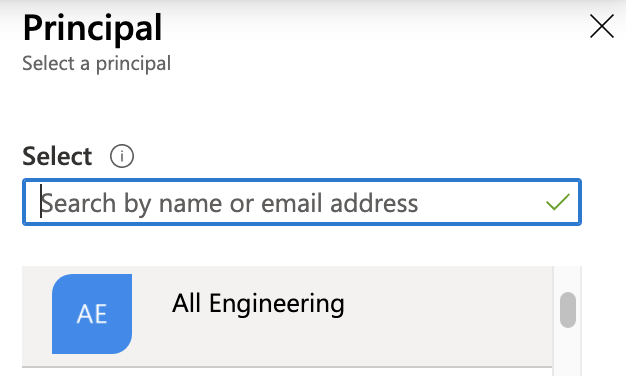
Click Select principal.

In the resulting Principal pane at right, enter the name of the App registration whose Client ID, Tenant ID, Key, and Vault you’ve entered (above) in Harness Manager.
Click Select to select this App registration.
Repeat the above steps (as needed) to make your other vaults writable.
Option: Use Existing Azure Key Vault Secrets
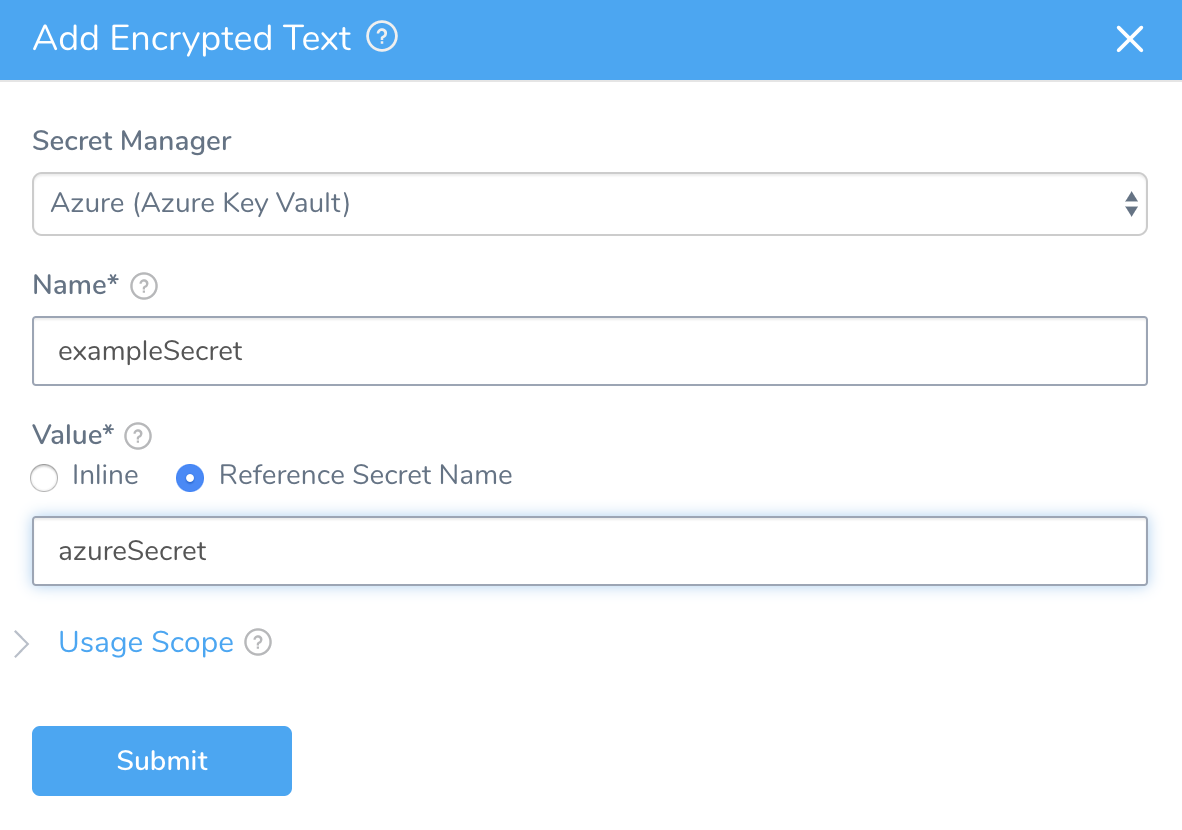
You can create a Harness secret that refers to an existing secret in Azure Key Vault, using that secret's name (for example: azureSecret). You can also specify the secret's version (for example: azureSecret/05).
Next Steps
- Refer back to Secrets Management for other secrets storage options.